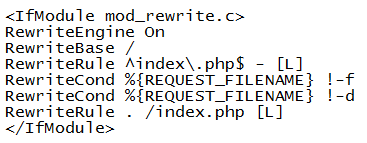
Recently we learned that the newest version of Chrome will no longer support an antiquated Netscape API. Basically this disabled Java applications from running within Chrome. As we’re in the midst of mandated State Pearson testing, this break resulted in significant problems for our students.
According to a recent Google Chromium thread this feature is being deprecated totally in September 2015.
In September 2015, Google will remove the override and NPAPI support will be permanently removed from Chrome. Installed extensions that require NPAPI plugins will no longer be able to load those plugins.
Issue 477112: Latest Java not working with Chrome 42
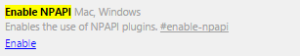
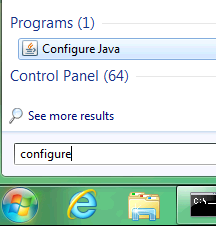
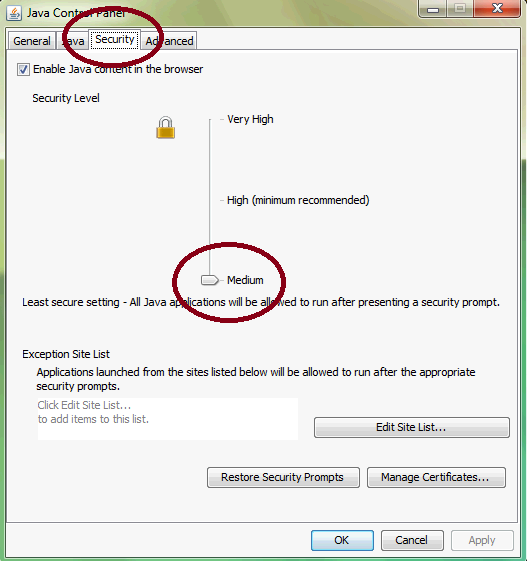
There is a simple solution, which is to re-enable the NPAPI plugin. That setting can be found below
![]()